This PowerShell script setups your Windows Computer to support TLS 1.1 and TLS 1.2 protocol with Forward secrecy. Additionally it increases security of your SSL connections by disabling insecure SSL2 and SSL3 and all insecure and weak ciphers that a browser may fall-back, too. This script implements the current best practice rules. It was originally written for Microsoft Internet Information Server 7.5/8.0/8.5/10 (IIS) on Windows 2008R2/2012/2012R2/2016/2019, but the below settings implements system wide settings that work for everything that uses the Microsoft Crypto infrastructure. This means Microsoft Exchange and Internet Explorer and Edge and all applications that use WinHTTP API, too. It works on both Windows Desktops and Servers.
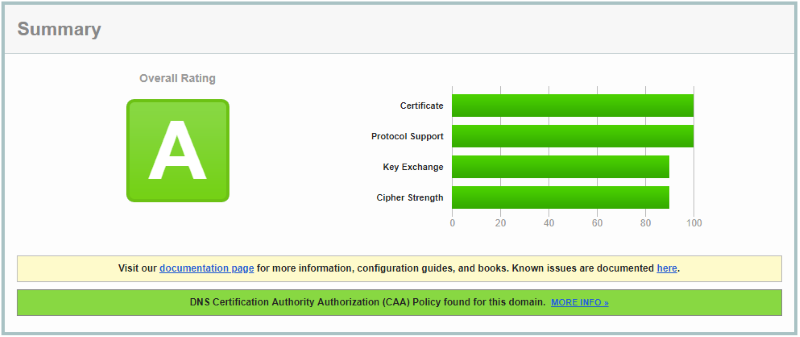
After you have added below registry entries you may like to verify that your server offers the much more secure SSL connections. There is the great https://www.ssllabs.com/ssltest/ site that gives you a feeling how secure your SSL connections are. You should get a Summary like these: