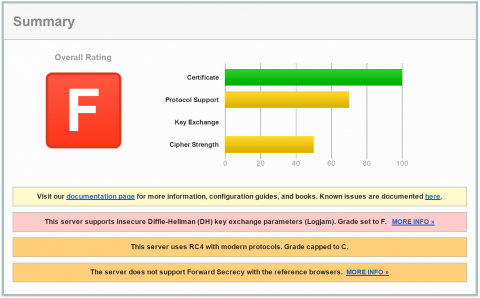
I just installed a Web Console on Windows 2012 R2 Core server and learned how insecure this system is out of the box. You may have worked through the Post-Installation Configurations for Web Server and Web Console. This ends with an highly insecure web server configuration. The SSL encryption is sooo weak that I tend to say you can also leave SSL switched off. You can check your server with SSL Server Test. Commvault default with Java 7 will end with the most worse test result of F.
What happened?
Out of the box Commvault installs a Java 1.7.0.17. A Java version that is officially no longer supported by Oracle since April 2015. Only Java 8 is supported. On the encryption side Java 7.x is a mess today. It has many weak ciphers enabled like RC4 and also supports diffie hellman key exchange with less than 2048 bit. The latest Web Console has a Tomcat 7.0.61 embedded that supports a lot better encryption level with Java 8. Commvault does not tell us how to install Java 8 on Windows CORE and they also document insecure server configurations. They also leave you standing in the rain if you need help and tell them about.
Commvault documentation says you should install latest Java JRE, but if you ever tried to install Java JRE 7 or Java JRE 8 on a Windows Core server you know this will fail. There are also some articles on the net that may tell you the lie that it can be installed with SILENT install, but this is incorrect. Just try it with logging enabled and you will end with a corrupted install that failed in the logs. The full uninstall part and I don't know what else is missing in registry. This does disallow you to uninstall it later. Upgrades to later Java JRE versions will also fail and become a real challenge. Good luck if you made this mistake!
I have found only one way to install Java 8 on Windows Core as of today. You need to download JDK package. If you install this you need to deselect Source Code and JRE. Only install the JDK part. This will succeed and you can also uninstall it later.
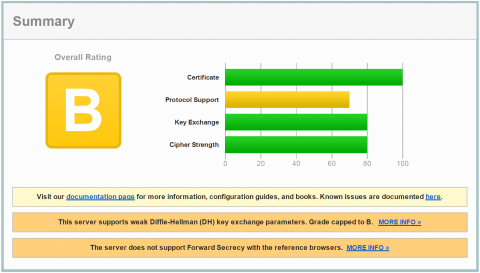
How will this SSLLabs test result looks like with Java 8?
That is much better, but we can get more without loosing or blocking any current client computers:
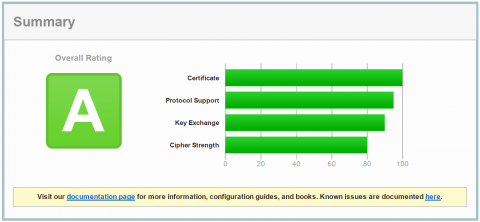
So far so good. What need to be changed to reach these secure "A" configuration that also uses Perfect Forward Secrecy with all browsers?
- Install latest Java 8. I strongly recommend Windows Core to reduce the patch burden on this public machine. You will have a lot less patches to install on non-GUI versions. On Windows core you need to install JDK8 without Source Code and JRE.
C:\Install\jdk-8u92-windows-x64.exe ADDLOCAL=ToolsFeature /s /L C:\install_jdk-8u92-windows-x64.log
- Stop Tomcat server in:
"C:\Program Files\CommVault\Simpana\Base\Gxadmin.exe"
- Configure the Tomcat service by running the command:
"C:\Program Files\CommVault\Simpana\Apache\bin\tomcat6w.exe" //ES//GxTomcatInstance001
- Uncheck the use of default JRE 1.7
- Configure Java Virtual Machine to use Java 8 JDK:
C:\Program Files\Java\jdk1.8.0_92\jre\bin\server\jvm.dll
- To get an "A" test result you need to disable insecure diffie hellman ciphers with less than 2048bit. This is done by adding below extra line to the Java Options:
-Djdk.tls.ephemeralDHKeySize=2048
- Configure
C:\ProgramFiles\CommVault\Simpana\Apache\conf\server.xml. This configuration works with every Tomcat 7.0.60+ with Java 8.<Connector protocol="HTTP/1.1" connectionTimeout="600000" redirectPort="443" URIEncoding="UTF-8" maxPostSize="40960000" maxHttpHeaderSize="1024000" maxThreads="2500" enableLookups="true" port="80" /> <Connector protocol="org.apache.coyote.http11.Http11NioProtocol" port="443" connectionTimeout="600000" URIEncoding="UTF-8" maxPostSize="40960000" maxHttpHeaderSize="1024000" maxThreads="2500" enableLookups="true" SSLEnabled="true" scheme="https" secure="true" clientAuth="false" keystoreFile="C:/Program Files/CommVault/Simpana/Apache/tomcat_webconsole.example.com.pfx" keystorePass="changeit" keystoreType="PKCS12" sslProtocol="TLS" sslEnabledProtocols="TLSv1,TLSv1.1,TLSv1.2" useServerCipherSuitesOrder="true" ciphers="TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_DHE_RSA_WITH_AES_128_GCM_SHA256,TLS_DHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA,TLS_DHE_RSA_WITH_AES_128_CBC_SHA256,TLS_DHE_RSA_WITH_AES_128_CBC_SHA,TLS_DHE_RSA_WITH_AES_256_CBC_SHA256,TLS_DHE_RSA_WITH_AES_256_CBC_SHA,TLS_RSA_WITH_AES_128_GCM_SHA256,TLS_RSA_WITH_AES_256_GCM_SHA384,TLS_RSA_WITH_AES_128_CBC_SHA256,TLS_RSA_WITH_AES_256_CBC_SHA256,TLS_RSA_WITH_AES_128_CBC_SHA,TLS_RSA_WITH_AES_256_CBC_SHA,SSL_RSA_WITH_3DES_EDE_CBC_SHA" compression="on" compressableMimeType="text/html,text/plain,text/javascript,application/json,text/calendar" />
- Enabling HTTP Strict Transport Security (HSTS) is currently not posssible out of the box (January 2016). The Tomcat need to be updated by Commvault to 7.0.65 or later.
- Start Tomcat
- Make a check with SSL Labs and verify that you get an A.
It is a real shame from my point of view that Commvault does not have this documented in the linked article, but herby you can run a secure SSL configuration that implement the best practices as of today. You may need to remove SSL_RSA_WITH_3DES_EDE_CBC_SHA cipher in a year or so as 3DES is marked as potentially insecure in near future. This 3DES is the last secure cipher that Windows XP with IE 8 supports. If you need to support Windows XP you need this, otherwise you can remove it. Be warned that you must not remove TLSv1 for PCI compliance (forced per June 2018) as this will break at least Outlook 2010 integration. To solve this issue you need a Windows Update from Microsoft and need to add Update to enable TLS 1.1 and TLS 1.2 as a default secure protocols in WinHTTP in Windows.
Just a final note. If you may need to uninstall Java JDK you need to run this commands. The appropiate product code (GUID) of the version you installed can be found in the installation logfile or registry at HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\ and look for the UninstallString of your JDK version.
- JDK 8.65 Uninstall:
MsiExec.exe /X{64A3A4F4-B792-11D6-A78A-00B0D0180650} /qn /L C:\uninstall_jdk-8u65-windows-x64.log
- JDK 8.92 Uninstall:
MsiExec.exe /X{64A3A4F4-B792-11D6-A78A-00B0D0180920} /qn /L C:\uninstall_jdk-8u92-windows-x64.log
History
- 2018/03/26: Added note how to enable TLS1.1 and TLS1.2 for Microsoft Office.
- 2015/11/26: Created